Duplicate Registration - The Twinning Twins

I would like to share one of my unique finding about a bug called Duplicate Registration which led to Account Takeover. Using this bug it was possible to takeover any account with the same username.
Summary :
Duplicate registration is when an application allows us to register or sign up with the same email address, username or phone number. It can have critical consequences based on what kind of attack is performed.
I was looking for different bugs and just tried to register my self with the same email but it didn’t happen. So I tried to register myself with same username and it was successful. While logging in to the application they ask for username or email address, so as of now everything is fine. I then tried to exploit the password reset functionality where they asks you Which did you forget : Password or Username so after selecting password they will ask you to enter your username and then the link is sent to your email which means you can reset password of any account using only 1 email because the usernames are same and which also means you can takeover any of the account.
In this case when I changed the password it got changed for both the accounts because the usernames of both the accounts were same.
NOTE : In this web application all the profiles were public so it was easy to identify the usernames and emails of different users. For exploiting it on my end I created two trial accounts
Attack Scenario :
Phase 1 :
Let’s assume a victim register him/her self with the email (for eg. abc@gmail.com) and username as Bob, now as the profile is public an attacker can see his/her profile and he/she creates an account with same username Bob with different email address (for eg. xyz@gmail.com).
Phase 2 :
Now attacker uses password reset functionality where he/she was asked Which did you forget : Password or Username and attacker chose the option of Password, now the application will send the password reset link to attacker’s email (xyz@gmail.com) and he/she reset’s the password (which got changed for both the accounts because of the same username).
Phase 3 :
Now an attacker can login into both the accounts but using an email instead of username.
NOTE : An attacker needs to login using email because same usernames cannot have same password but different email addresses can have same password.
How I found this vulnerability ?
- I created an account on browser A (Firefox) with the username UserTwo

2. I created another account on browser B (Firefox Private) with same username UserTwo but with different email ID
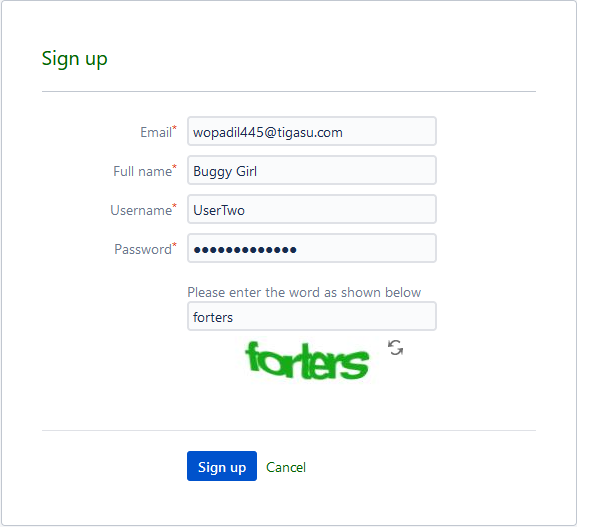
3. Now I logged in to first account on browser A (Firefox)


4. Then I logged into another account from browser B (Firefox Private)


5. I logged out and went to reset password page on browser A
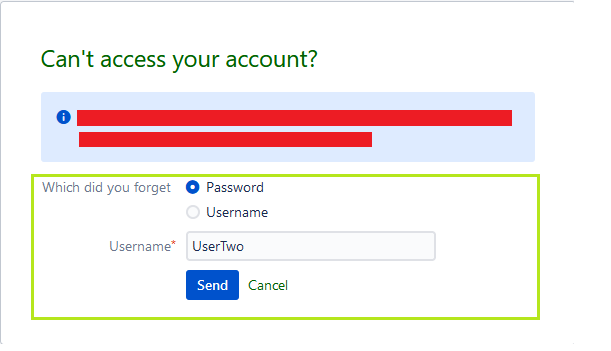
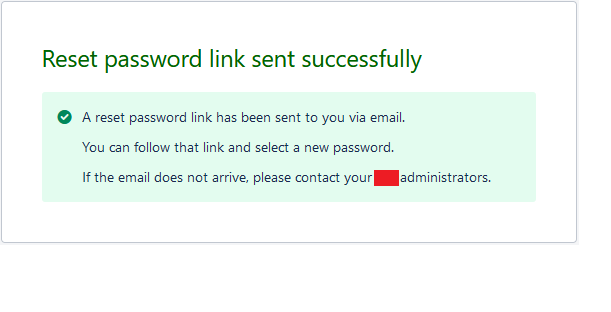
After resetting the password I was able to access both the accounts using different emails with same password.
Why It Happened ?
To know why this happened I sent the password reset link on both of my test accounts and found that the token that was used for password reset was same for both the accounts because the usernames of both the account were same.
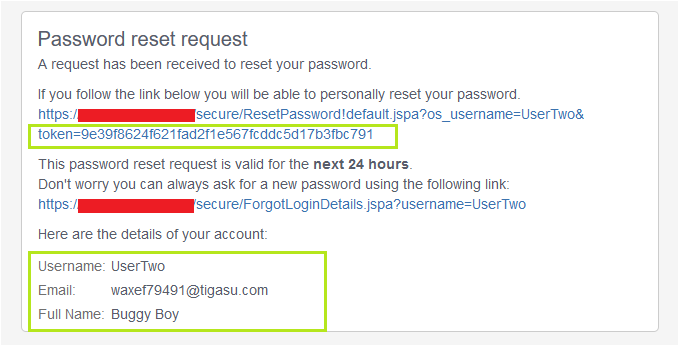
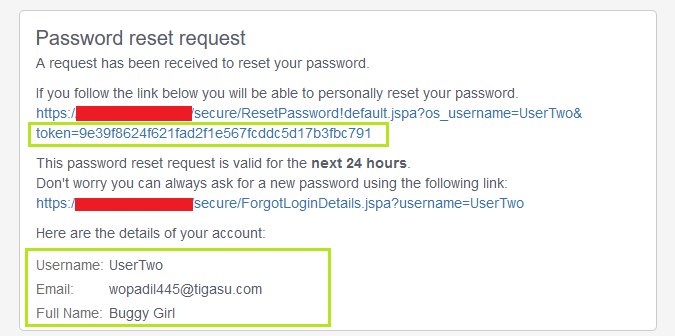
Here in the above screenshots you can see the the token and the username are same of both the accounts.
Impact :
Anyone can takeover the account of any user without his/her knowledge.
Mitigation :
An application should always check for duplicate entries of Usernames, Emails and Phone Numbers to avoid such kind of web application flaws.

