Shodan Dorks - The God’s Eye

Summary :
Shodan is a search engine for Internet-connected devices. It is different from search engines like Google and Bing because Google and Bing are great for finding websites but Shodan helps in finding different things like popular versions of Microsoft IIS, control servers for Malware, how many host are affected with the new CVEs, which countries are becoming more connected, SSL certificates of the websites etc.
Difference between Shodan and Google :
The major difference between Shodan and Google is that, that Shodan analyzes the internet and Google analyzes the Word Wide Web.
Description :
Shodan is the most popular search engine ever seen. It has the capability to index small desktops, CCTVs, nuclear power plants etc.
Nowadays shodan has become very popular in the world of penetration testing, bug bounties, digital forensics, threat hunting etc.
Shodan’s Search Query Insights :
Shodan gathers information by interacting with web services and this information is stored in an object called the banner, so when you search anything using a shodan dork (search query) shodan takes the information from the banner of that service and displays it to you. In simple words banner is a metadata about a service, for HTTP it means headers and for FTP it means welcome string. Different services have different banners, lets look at the example of vsftpd 3.0.3 and Siemens S7 banners.


Shodan has two versions :
1. Web Based
2. CLI Based
Shodan command line interface (CLI) uses python library for shodan. It is been said that shodan CLI is more powerful than web-based version. There is also a slight difference between the commands being used on web version and CLI version.
How to use Web Based version (Basics) ?
- Go to https://account.shodan.io/login?continue=http%3A%2F%2Fwww.shodan.io%2Fdashboard and login to your account

2. Enter your shodan dork (query) in the search bar and hit enter


4. You can also filter results using response codes

How to use CLI Based version (Basics) ?
- sudo apt install python python3 python-pip python3-pip
- sudo apt install python-setuptools python3-setuptools


3. sudo pip install shodan

4. After installation I ran the command shodan count microsoft iis 6.0 which gave me an error regarding the API key, so I ran the command shodan init <API-KEY> to configure my api key

Note : I took the API key from my shodan web account

5. Then I used the command shodan scan submit --force IP to scan specific IP using shodan cli

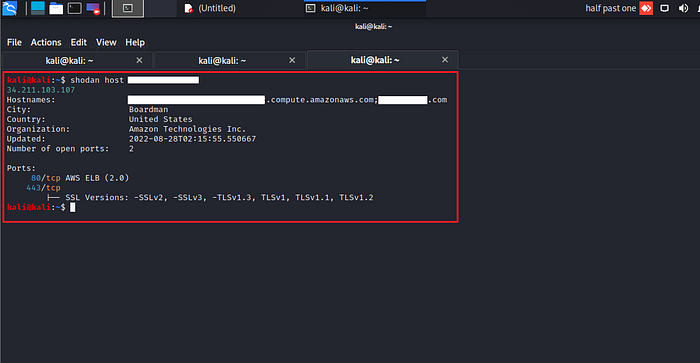
6. For searching specific host I used the command shodan host IP
Shodan Monitoring
Shodan monitoring helps you to monitor your target’s IP address. It can monitor single IP address, list of IP addresses or even net blocks (IP subnets). It will help you to identify industrial control systems, malware related services, uncommon services, open databases, iot devices, internet exposed services, expired ssl certificates, new services of your target and vulnerable cve for your target.
How to use shodan for network monitoring (CLI) ?
- Use the command shodan alert to check the available options

2. Then use the command shodan alert create “TargetName” <TargetIP> to add your target for network monitoring (you can also define IP range - net blocks instead of single IP)

3. Then use the command shodan alert triggers to check the available triggers


4. Then use the command shodan alert list to check the alert ID

5. Now for enabling the alerts for your target use the command shodan alert enable <alertID> <alertNames>

Domain-based Networking Monitoring
Sometimes it happens that we are not aware about the IPs or their network ranges we only have the domain name for testing so in that case shodan provides us with domain based network monitoring where we can directly use the domain name for monitoring instead of IP address or network ranges.
Instance :
- Use the command shodan alert domain <domainName>

The best part is that after giving the domain name shodan will automatically find all the subdomains and their IPs and will create a network monitor for them. It will keep the monitor up to date as the DNS information changes of your target and you can view your target information using the command shodan domain <domainName>
Instance :

How to use shodan for network monitoring (Web) ?
- Go to https://monitor.shodan.io/dashboard and click on “SETUP NETWORK MONITOR”

2. Add the name and IP address of your target (you can also add net range like 104.16.100.52/32) and click on Add Network

NOTE : Here in the right side you can see 16 IPs remaining which means I can only add up to 16 IP addresses, it is because I have academic membership. Different membership will have different benefits (check here : https://account.shodan.io/billing).
3. Now click on edit and scroll down to apply trigger rules and then click on Save Changes


NOTE : I have chose the trigger rules as per bug bounty. If you are doing a pentesting you can select all of them.
4. Then click on dashboard > browse results



Shodan as Browser Plug-in
Shodan has a variety of versions and till now we saw CLI based and web based versions of shodan but shodan can also be used as a browser plugin with limited functionalities compare to web and cli based versions.
Shodan browser plugin automatically detects that in which country or city the website is hosted, who owns the IP and what all services and ports are open. Apart from that it also gives you the SSL certificate, hostname, web technologies, organization name, ISP, ASN, domain records and subdomains of your target.
How to use browser plugin ?
- Go to https://chrome.google.com/webstore/detail/shodan/jjalcfnidlmpjhdfepjhjbhnhkbgleap/related and click on Add to Chrome

2. Click on Add extension

3. Now visit your target domain and click on the plugin


4. Then right click on View IP Details > Open link in new tab


5. For viewing domain details, right click on View domain details > Open link in new tab


Shodan Dorks Insights :
General
- org
This shodan dork is used to find all the assets related to your target domain and you can also use the filtering options to remove the output you don’t want. You can use this dork when your target domain or company has a wildcard domains in scope or all the products belong to target company is in scope.
2. product
This shodan dork is used to find the target based on the specific product, for e.g. if you want to find all the domains of your target that are using the product mongodb then you can use this dork.
3. net
This shodan dork represents the CIDR notation. It is used to find out the available hosts in particular subnets, for e.g. if your target IP address is 104.16.100.52/32, here 32 is the subnet of your IP and shodan will list down all the IP address that belong to this particular subnet.
4. asn
This shodan dork is used to find all the hosts/domains of your target company. ASN is autonomous number system which will find all the internet connected assets that belongs to your target company, for e.g. go to https://hackertarget.com/as-ip-lookup/ and enter the IP of your target and it will give you the ASN number of your target then use that asn number to search for your target on shodan.
5. hostname
This shodan dork is used to find all the internet connected hosts of your target, for e.g. you entered your target as www.hackerone.com then this dork will find all the hosts with this name connected on the internet.
6. ip
This shodan dork will help you to find all of your target host that has the IP address you provided, for e.g. your ip is 104.16.100.52 then this dork will find all the hosts that belongs to particular IP.
7. all
This shodan dork is used to find all the results for the name that is passed in this dork. for e.g. if you want all the results related to tesla then this dork will help to find it out.
8. port
This shodan dork is used to find the vulnerable open ports of your target website which might leak sensitive information
HTTP
- http.component and http.component_category
There is a small difference between http.component and http.component_category where http.component is the name of the technology that is being used by the website for e.g. wordpress, jquery, mysql, nginx etc. and http.component_category is the name of the category of the components being used for e.g. cms, javascript libraries, databases, web servers etc.

2. http.favicon.hash
The favicon is a small icon displayed in the browser’s address bar or tab used for branding a website and we can calculate the hash of that icon by download the favicon.ico file. That hash can be used in shodan’s http.favicon.hash dork to find out the available exploit.
3. http.html
This dork is used to find the technologies and words in the source code of your target website for e.g. you want to search that the website is using drupal 8.0 or not, then you can simple pass the value in this dork and it will give you the results.
NOTE 1 : This dork is used when you know that the a particular technology’s (drupal) version is vulnerable to a particular cve.
NOTE 2 : This dork is used when your target has a huge scope of subdomains.
4. http.title
This dork is used to find whatever is written between the <title> tag of html in the website. for e.g. if you want to find the website that has grafana as a title you can use this dork. A small difference between http.title and http.html is that, that http.html will give you more results compare to http.title, so you can use either of them

5. http.status
This dork is used to filter out the outputs based on the status code of your target for e.g. 200, 403, 301, 302, 401 etc. You can also used the status code directly without using this shodan dork, just append the status code using a + symbol but it will then search for all the possible 200 values and in the result, not only limited to status code.
6. http.waf
This dork is used to filter out your target according to web application firewall. for e.g. your target web application is using Barracuda firewall then you can use this dork to find which all web application domains of your target are using this firewall.
NOTE 1 : This dork is used when you know that a particular payload or technique exists to bypass this firewall.
NOTE 2 : This dork is used when your target has a huge scope of subdomains.
SSL
- ssl.alpn
Application-Layer Protocol Negotiation (ALPN) is a Transport Layer Security (TLS) extension that allows the application layer to negotiate which protocol should be performed over a secure connection. This dork can be used to identify which ALPN is being supported by the requests of your target domain. for e.g. if your target request has HTTP/2.0 and you want to check whether it supports HTTP/1.0 or HTTP/1.1 then you can use this dork.
NOTE 1 : This dork is used when you want to check for http desync/smuggling attacks
NOTE 2 : This dork is used when your target has a huge scope of subdomains.
2. ssl.cert.subject.cn and ssl.cert.issuer.cn
There is a small difference between ssl.cert.subject.cn and ssl.cert.issuer.cn where ssl.cert.subject.cn is the name of your target company or organization and ssl.cert.issuer.cn is the company that issues and verifies the certificate provided to your target company or organization.
NOTE 1 : This dork ssl.cert.issuer.cn will not be used in bug bounty.
Custom Dorks
- set-cookie
This custom shodan dork is used to find the values that a cookie of your target company’s request contains.
2. x-drupal-cache
This custom shodan dork is used to find for drupal caching issues for your target website.
3. access-control-allow-origin
This custom shodan dork is used to find the cross origin resource sharing issues for your target website.
4. WWW-Authenticate
This custom shodan dork will help to find the authentication related issues for your target website.
5. X-Magento-Cache-Debug
This custom shodan dork is used to find for magento caching issues for your target website.
6. kbn-name
This custom shodan dork is used to find the kibana applications for your target website.
7. x-forwarded-for and x-forwarded-host
This custom shodan dorks are used to find the header injection issues for your target website.
8. x-jenkins
This custom shodan dork is used to find the jenkins server for your target website.
NOTE 1 : You need to enumerate and look for the vulnerabilities. This dorks will not give you the direct hit to vulnerabilities.
NOTE 2 : This dorks will help you to know what vulnerabilities you can find on your target domains, if any of your target is using the above mentioned headers.
Shodan Dorking Usage Diagram

Shodan Dorking (Web)
org:”target.com”
http.status:”<status_code>”
product:”<Product_Name>”
port:<Port_Number> “Service_Message”
port:<Port_Number> “Service_Name”
http.component:”<Component_Name>”
http.component_category:”<Component_Category>”
http.waf:”<firewall_name>”
http.html:”<Name>”
http.title:”<Title_Name>”
ssl.alpn:”<Protocol>”
http.favicon.hash:”<Favicon_Hash>”
net:”<Net_Range>” (for e.g. 104.16.100.52/32)
ssl.cert.subject.cn:”<Domain.com>”
asn:”<ASnumber>”
hostname:”<hostname>”
ip:”<IP_Address>”
all:”<Keyword>”
“Set-Cookie: phpMyAdmin”
“Set-Cookie: lang=”
“Set-Cookie: PHPSESSID”
“Set-Cookie: webvpn”
“Set-Cookie:webvpnlogin=1”
“Set-Cookie:webvpnLang=en”
“Set-Cookie: mongo-express=”
“Set-Cookie: user_id=”
“Set-Cookie: phpMyAdmin=”
“Set-Cookie: _gitlab_session”
“X-elastic-product: Elasticsearch”
“x-drupal-cache”
“access-control-allow-origin”
“WWW-Authenticate”
“ X-Magento-Cache-Debug”
“kbn-name: kibana”
“X-App-Name: kibana”
“x-jenkins”
URLs for Shodan Dorks (Web)
- http.html
https://gist.github.com/JerryShah3/8e25ecfeb9fa88784aa274d97b3cf86f
2. http.title
https://gist.github.com/JerryShah3/ccd9c8bd7eafa52b69f5a76917eec074
3. http.status
https://gist.github.com/JerryShah3/e4018ecce48eefcb8e02ebadf9468ae8
4. port
https://gist.github.com/JerryShah3/7c5cb2f25ceb3e522bfdfd0f9a68f6bb
5. http.favicon.hash
https://gist.github.com/JerryShah3/9eb4189b9b450d32c229b9c0cfbe3988
6. http.component
https://gist.github.com/JerryShah3/95d3a1baf2d29973286effb491684297
7. http.component_category
https://gist.github.com/JerryShah3/71bbbd368af846304e8588747984663b
8. http.waf
https://gist.github.com/JerryShah3/db7e47d1497d64e80c841961f3fb48b3
9. ssl.alpn
https://gist.github.com/JerryShah3/91c9fc5116bd58d3f92a454cb544b4f3
10. product
https://gist.github.com/JerryShah3/82346509de0208cf0d932e92bf20f0db
Shodan Dorking (CLI)
shodan host <IP>
shodan stats — facets port,org ssh
shodan domain <domain-name>
shodan honeyscore IP
shodan alert create “HackerOne” 104.16.100.52 (It will create an alert for the IP and will also provide an alert ID)
shodan stats --facets org discourse
shodan download --limit -1 <filename> ‘title:”IBM”’
shodan parse --fields ip_str,port,org --separator , filename.json.gz (to see the downloaded file contents by filtering it)
shodan domain hackerone.com
shodan honeyscore IP
shodan alert create “HackerOne” 104.16.100.52 (It will create an alert for the IP and will also provide an alert ID)
shodan alert create “Hyatt Hotels” 140.95.0.0/16
shodan alert enable <alert ID> new_service,open_database,vulnerable,ssl_expired,internet_scanner,uncommon
shodan alert hackerone.com
NOTE : I have not used the CLI version much so I have included the CLI dorks that I know and I have used.
Special Thanks for Proof Reading and Contributing in Dorks : Jinay Patel

